TL;DR
In this episode, you’ll learn how to secure your online accounts with rock-solid authentication methods as a solopreneur.
First, we’ll explore different types of authentication, from basic PINs to advanced biometrics.
Then, we’ll provide practical tips for creating and managing passwords that will make hackers give up.
Finally, we’ll introduce you to passkeys, the latest innovation in tech that’s gaining attention.
Useful links
Tools mentioned in this episode
- 🆓 Mac Security Checklist: https://macpreneur.com/msc
- 1Password:
- EU: https://1password.eu
- Canada: https://1password.ca
- Rest of the world: https://1password.com
- Bitwarden: https://bitwarden.com
Past episodes mentioned during the show
Understanding Authentication Methods
PIN Codes: The Basics and Risks
PIN codes are typically 4, 5, or 6 digits.
This method is the least secure due to the limited number of possible combinations.
Plus, people often choose non-random numbers like birth years, dates, or zip codes.
In episode 974 of the Security Now Podcast, host Steve Gibson discussed an infographic displaying a heat map of 3.4 million four-digit PIN codes from data breaches.
The infographic uses a square matrix with the first two digits (0-99) on the vertical axis and the last two digits (0-99) on the horizontal axis. The whiter the square, the more frequently the PIN appears.
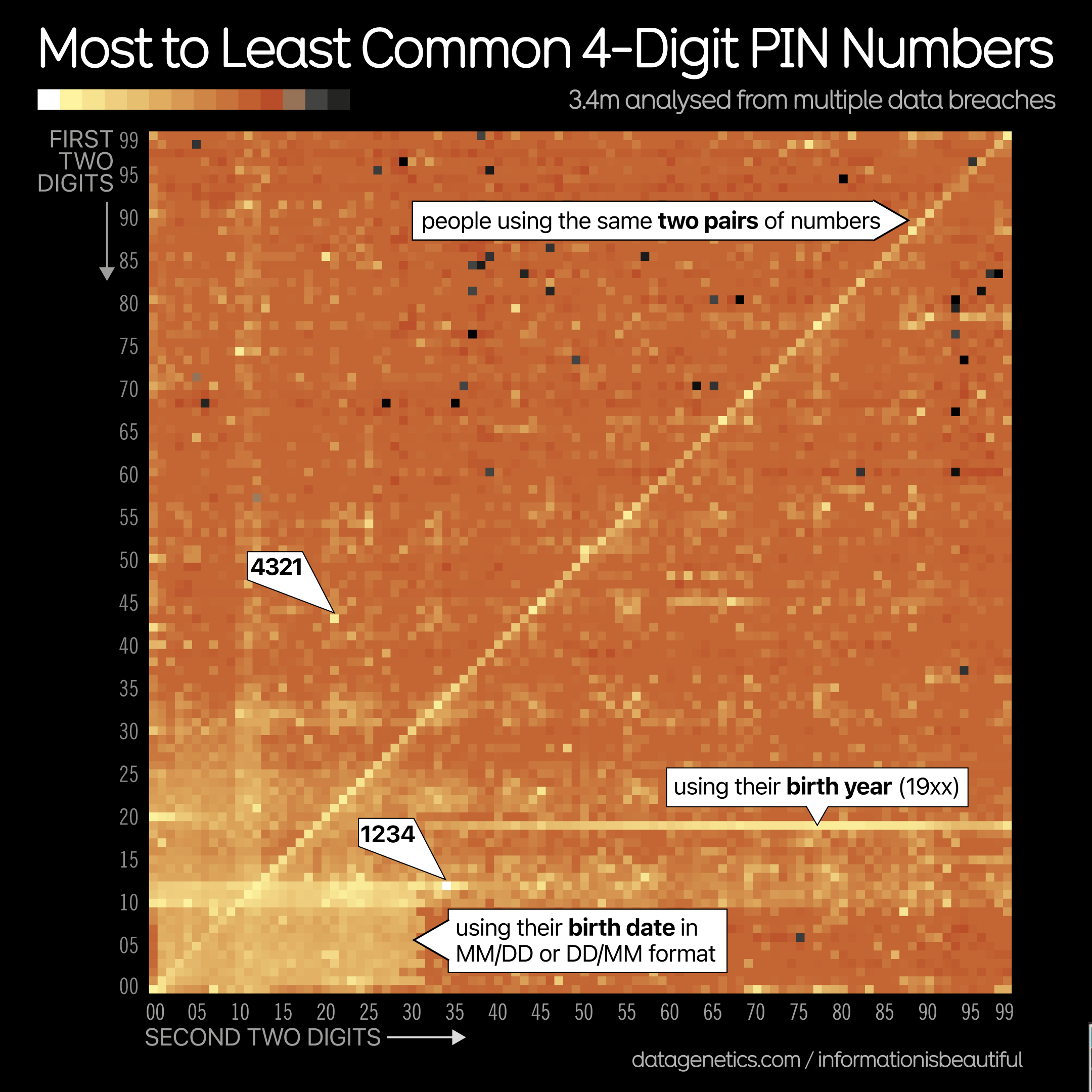
Unsurprisingly, common PINs like 1234 and 4321, as well as birth years, are very popular. Many people also use repeated pairs like 3737 or 6262.
Hackers exploit this by first trying the most common PINs, which often gives them quick access.
If that fails, they use a brute force attack, trying all possible combinations. With only 10,000 combinations for a four-digit PIN, cracking it usually takes just a few minutes.
The same goes for five and six-digit passcodes. Even a six-digit code can be easily observed and remembered.
So, always cover the keypad when you enter your PIN to keep it secure.
Username and Password: Best Practices
This is the most common way to authenticate, especially online.
The username is usually an email address, but sometimes you can pick something else.
For the password, it’s best to make it long and random.
Unfortunately, some sites limit password length or restrict certain symbols, which can make brute force attacks easier.
I’ll talk about techniques and tools to create and manage strong passwords later in this blog post.
Biometric Authentication: How It Works
This method uses something unique about you, like your fingerprint, face, retina or iris, or voice.
In the Apple ecosystem, this is done through Touch ID or Face ID.
Only one can be used at a time, and the device never stores the actual fingerprint or face.
Instead, it keeps a mathematical representation in a secure part of the chip called the secure enclave, which can’t be accessed directly.
Here’s how it works: When you try to authenticate, the sensor creates a new mathematical representation and checks it against the one stored in the secure enclave.
With Touch ID, there’s a 1 in 50,000 chance that another fingerprint could match yours because the sensor only scans certain parts of the fingerprint. This allows it to work no matter which part touches the sensor. It’s a good idea to have your children try unlocking your devices, as fingerprints can be somewhat hereditary.
With Face ID, the chance of a mistaken match is only 1 in a million unless the person is an identical twin or almost a perfect lookalike. Face ID projects about 30,000 infrared dots to create a 3D model of your face, which is why it works even in the dark.
For most uses, biometric authentication is combined with another method, like a PIN or password, especially for physical security like data centers.
Passwordless Authentication: The Future
After you enter your username, you authenticate using an email loop, a physical key, or a passkey.
This method has the advantage that the server doesn’t need to store a secret.
Email loop: The server sends a unique login link or code that can only be used once and expires quickly.
Physical security key: The server creates a public key that it stores, while you keep a private key on a physical device. Even if the server leaks the public key, no one can sign in without your private key.
I use a YubiKey from Yubico and recently bought another from Token2, which supports USB C, USB A, and NFC.
Two keys are required to activate this level of protection on an Apple account.
Passkeys: This new technology also uses public and private keys but operates at the software level.
Passkeys can be stored in iCloud Keychain or a password manager.
I’ll cover passkeys in more detail later in this blog post.
Multi-Factor Authentication (MFA): Adding Layers of Security
MFA combines three elements: something you know, something you are, and something you have.
- Something you know: This is usually a PIN, username, or password.
- Something you are: This is biometric authentication, like your fingerprint or face.
- Something you have: This can be a device already connected to the account, a device that receives codes via SMS or directly from a server, a dongle or app that generates 6-digit codes, or even a physical security key or passkey.
Creating Strong Passwords: Techniques and Tools
What makes a strong password?
A strong password is:
- long, ideally at least 16 characters
- complex, combining digits, uppercase and lowercase letters, and symbols
- unique, which is best achieved by generating a completely random password for critical accounts that you don’t need to memorize.
However, for some accounts, a strong but memorable password makes sense, like for Google Workspace, iCloud, and your password manager.
So, how can we create a memorable password that’s also hard to guess or brute force?
Padding Technique:
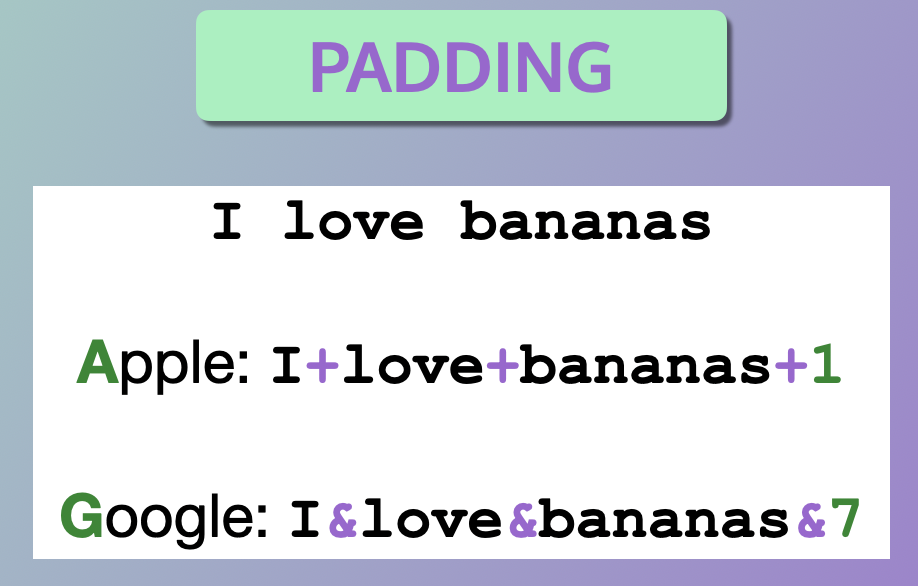
Start with an easy-to-remember sentence and add symbols at the beginning, middle, and end.
For example, “I love bananas” could become “I+love+bananas+1” for an Apple account password.
For a Google password, you might use “I&love&bananas&7”.
These passwords are long and complex, making them difficult to guess, even if they’re not completely random.
Passphrase Technique:

Use a longer sentence, like the start of a favorite book chapter, and shorten it.
For example, “There are 12 months and 365 days in a year” can be shortened to “T12m&365diay”.
Adding a symbol and the service name, like “-APL” for Apple, makes it even stronger.
For most accounts, especially those at high risk of being hacked, it’s best to use totally random passwords.
Big companies like Google and Apple have strong security, but I’m less confident in others.
Assume that eventually, your username and password will get leaked.
Creating Random Passwords:
The simplest way is to use Safari’s suggested passwords when creating an account.
These are strong and saved in iCloud Keychain, syncing across all your Apple devices.
Other browsers can suggest strong passwords too, but iCloud Keychain is more secure for managing them.
Another option is using Keychain Access if you need to generate and store passwords exclusively on your Mac without syncing them.
Keychain Access is built into macOS.
To open it, use Spotlight by pressing Command + Space and typing “Keychain Access,” or find it in the Utilities subfolder within Applications.
To create a new item:
- Select the Login keychain in the left sidebar, then click the square with a pen icon in the top toolbar.
- Enter the login URL or service name in the top field, and your username in the Account Name field.
- To generate a password, click the key icon to open the Password Assistant.
- Choose Random from the dropdown menu and adjust the slider for the desired length.
- Close the Password Assistant and click Add to save.
To use the password:
- Open Keychain Access
- Select the Login keychain, and search for the service or account name.
- Right-click the item and select Copy Password to Clipboard.
- You’ll need to enter your Mac user account password and click Allow before pasting the password where needed.
Remember, these passwords are protected by your user account password and only accessible from that Mac. Ensure they are backed up with Time Machine to prevent data loss.
By Fall 2024, Apple will introduce a standalone Passwords application. The Mac version looks similar to the Reminders app, and the iPad version will be almost identical. I’m waiting for a public beta to test the iPhone version.
Third-party password managers
Is it still worth using a third-party password manager if Apple offers its own password management app?
Yes, it is. Here’s why:
Compatibility with Older macOS Versions: If your Mac runs a version older than macOS 15 Sequoia, iCloud Keychain and Keychain Access have a limitation of associating only one URL per item. This is inconvenient for users with accounts on multiple regional websites like Amazon.
Custom Fields: Third-party password managers allow you to create custom fields, such as secondary addresses, recovery phone numbers, or API keys, which iCloud Keychain doesn’t support.
App Passwords: When using iCloud Mail and needing to configure another email client, a third-party password manager lets you add an app password to the same item, avoiding multiple entries.
Storing Various Items: These managers can store additional types of items like passport information, driver’s licenses, bank account numbers, and documents. For instance, 1Password allows you to attach multiple documents to a single item.
Cross-Platform: Third-party managers like 1Password and Bitwarden are cross-platform, useful if you work with someone who doesn’t use Apple devices.
Server Location Choice: With options like 1Password and Bitwarden, you can choose the server location for your vault, essential for businesses under GDPR regulations. Bitwarden even allows hosting the vault on your own server.
Recommendations:
- 1Password: Known for its user-friendliness and robust features, but it requires a subscription. The individual plan is $36/year, and the family plan is $60/year. It supports Apple Watch unlock and keyboard shortcuts, enhancing efficiency.
- Bitwarden: Offers a free version with more features than iCloud Keychain. The premium plan is $10/year, and the family plan is $40/year for 6 members.
Advice: Start with iCloud Keychain for six months. If it meets your needs, continue using it. Otherwise, consider Bitwarden or 1Password. If you appreciate Apple Watch unlock or keyboard shortcuts, 1Password is the best choice, offering convenience and efficiency.
Exploring Passkeys: The Next Step in Authentication
Are you ready for a password-free future?
Imagine never having to type another password for your online accounts.
Passkeys offer this convenience, acting like a personal security guard for each of your online accounts.
With macOS 13 Ventura, iOS 16, and iPadOS 16, Apple devices started supporting Passkeys. And since iOS 17 and macOS 14 Sonoma, you can even share groups containing Passkeys with other Apple users.
So, what exactly are Passkeys?
They’re a new way to log in using your device’s biometric authentication, like Face ID or Touch ID, to pass a security challenge.
Unlike traditional usernames and passwords, websites don’t need to store any secrets, making it safer in case of data breaches.
Plus, a Passkey for a site like Facebook won’t work on a phishing site because it’s tied to Facebook’s domain.
Despite these benefits, Passkeys haven’t become widespread.
One reason is platform lock-in. If you store Passkeys in iCloud Keychain, you can only use them on Apple devices. To use them across different platforms, you need a third-party password manager like 1Password or Bitwarden.
Another challenge is that few websites support Passkeys, and many still offer traditional login methods. For example, in Google Workspace, Passkeys by default replace only the second authentication factor, not the username and password. Admins need to enable settings to fully replace usernames and passwords.
While Passkeys are a step forward in online security, they also shift the security responsibility to us and our devices. If someone gains access to our device and reconfigures biometric settings, they can use our Passkeys to access our accounts.
Final Tips and Action Plan for Strong Email Security
Before we wrap up, there’s one last crucial point to discuss: securing your email accounts.
Email Security Essentials
Email accounts are more critical than ever, especially as the trend moves towards passwordless authentication methods.
Your inbox password must be extremely strong and complex, and multi-factor authentication (MFA) is essential.
Avoid SMS-based MFA and opt for a physical security key.
Bonus Tips
- List Your Critical Services: Write down all your essential online services (e.g., domain registrar, website host, accounting platform) and the corresponding email addresses. This will help you see what needs the most protection.
- Use Google Workspace: If you’re a Google Workspace user, use the ‘Sign in with Google’ feature. This makes it harder for hackers, as they would need to breach your Google account first, which should be well-protected.
- 1Password Integration: If you use 1Password, it can track which services use ‘Sign in with Google’ and even identify the associated Google account. This is one reason why 1Password is highly recommended.
Action Plan for Stronger Authentication
- Enable Two-Factor Authentication (2FA): Do this for all your crucial accounts.
- Use a Password Manager: iCloud Keychain, 1Password, or Bitwarden are excellent choices.
- Adopt Passkeys: Start using passkeys where available to stay ahead.
- Secure Your Email: Treat your email accounts like Fort Knox—they are the keys to your digital kingdom.
Mac Security Checklist
Implementing strong authentication is not just about protecting your business—it’s about protecting your peace of mind.
You’ve worked hard to build your business, so don’t let weak security be your downfall.
Securing your online accounts is just half the battle. The other half is keeping your devices, especially your Mac, secure.
For this, follow the Mac Security Checklist covered in Episode 99.
If you haven’t downloaded it yet, visit macpreneur.com/msc.
If you need help with the checklist, listen to or watch Episode 99.
Your future self and your clients will thank you for taking proactive steps against cyber threats.
Upcoming Changes to the Macpreneur Podcast
Season 5 will conclude with Episode 107, which is set to release on July 25th, 2024.
After that, I’ll be taking a few weeks off for vacation starting in August, which means there will be a brief hiatus in regular programming.
But don’t worry—the podcast feed won’t be empty! During the break, I’ll be rebroadcasting some of the most popular and timeless episodes from Season 1. These are great episodes that many of you might have missed or forgotten about.
Season 6 is scheduled to kick off in September. For this season, I’m switching back to an interview format. I already have one episode recorded and several more in the works.
If you’d like to be a guest on the podcast, just head over to macpreneur.com/apply, fill out the application form, and I’ll get back to you within a few days.
I would love to hear about how you run your solopreneur business on your Mac, and what tips, tools, and strategies you use to be more efficient.
Conclusion and next
So that’s it for today.
In the next episode, I will discuss how solopreneurs can secure their business website.
So make sure to subscribe or follow this podcast to get it automatically next week.
Cheers,
Damien
FULL TRANSCRIPT (Click here)
Effortless Security: Say Goodbye to Weak Passwords Forever!
Introduction: Securing Your Digital Empire
Ever feel like your online accounts are a house of cards, ready to topple at any moment? You’re not alone. Today, we’re tackling the million-dollar question: how can busy solopreneurs like you implement rock-solid authentication without losing your mind?
Stick around because by the end of this episode, you will have a clear roadmap to secure your digital empire.
Plus, I will reveal a game-changing technology that might just make passwords obsolete. I’ll unpack all of this after the intro.
Welcome to Macpreneur Podcast
Hello, hello, and welcome to episode 105 of the Macpreneur podcast. Whether it’s your first time or you’re a long-time listener, I appreciate that you carve out some time in your busy solopreneur schedule. I’ve created Macpreneur to help as many solopreneurs as possible save time and money running their businesses on their Macs.
Now, in order to give you the most relevant Mac productivity tip and information, I need to know how well you’re currently dealing with the three killers of Mac productivity, namely unnecessary clicks, repetitive typing, and file clutter. For that, just visit macpreneur.com/tips and answer a few questions, which will take you less than two minutes.
After submitting your answers, you will receive personalized time-saving tips based on your results. Once again, visit macpreneur.com/tips and start boosting your efficiency today.
Understanding Authentication Methods
As a solopreneur juggling client work, social media marketing, and taking time to work on your business, you know the importance of protecting your digital assets.
But let’s be real. Implementing strong authentication can feel like trying to solve a Rubik’s Cube blindfolded. You might know it’s crucial, but where do you even start?
Fear not, because we’re going to break this down into bite-sized pieces. First, we’ll cover the different types of authentication, from basic pins to cutting-edge biometrics.
Then we’ll dive into practical strategies for creating and managing passwords that would make a hacker weep. And finally, we’ll explore passkeys, the new kid on the block that’s turning heads in the tech world.
PIN Codes: The Basics and Risks
So let’s start with a quick rundown of authentication methods, from least to most secure.
The first one is the PIN code, usually made of 4, 5, or 6 digits.
It’s the least secure method because the total number of potential codes is very limited. Plus, humans tend not to choose totally random numbers. Instead, they will be using their birth year or their birth date, zip code, and so on.
During episode 974 of the Security Now Podcast, the host Steve Gibson shared an infographic showing a heat map of 3.4 million four-digit PIN codes that were extracted from data breaches. In this case, the more a PIN code has been found, the whiter it is in the infographic, which consists of a square matrix with the first two digits going from zero to 99 along the vertical axis, and the last two digits, again from zero to 99 along the horizontal axis.
Now, if you’re listening to the audio version of the podcast, either visit https://grc.sc/pin, or check out episode 105 of the Macpreneur podcast on the YouTube channel.
Now, unsurprisingly, 1, 2, 3, 4, and 4, 3, 2, 1 are among the most common PIN codes, as well as the birth year.
And also, what’s striking is that a lot of people are using two pairs of numbers for their PIN, for instance, 37, 37, or 62, 62.
And so knowing that, what hackers will do is, first, they will try the most commonly used four-digit PIN codes, and the probability they will get in is very high.
And if that doesn’t work, the next step is to try out all the possible combinations, which is also called a brute force attack.
And given that there are only 10,000 possible combinations, it usually takes a few minutes to crack. It’s the same thing for five and six-digit passcodes. And since the human brain can easily hold up to 7 objects in short-term memory, even a 6-digit passcode can be easily discovered through direct observation.
In other words, always, always cover the keypad when you type a PIN code.
Username and Password: Best Practices
Number 2: Username and password.
This is the most common form of authentication, especially for online accounts.
The username is often an email address, but in some cases, you can choose something else.
For the password, the longer and more random it is, the better.
Now, some sites impose restrictions on the maximum length and the use of certain symbols, which unfortunately make brute force attacks more likely to succeed.
I will cover techniques and tools to create and manage strong passwords later in this episode.
Biometric Authentication: How It Works
Number three, biometric authentication. In a nutshell, it is something that you are: your fingerprint, your face, the retina or the iris, or your voice.
In the Apple world, it is either Touch ID or Face ID, never both at the same time. And in both cases, the device never stores our fingerprint or our face, but a mathematical representation of them.
And it is stored in the secure enclave, it’s a special area inside the chip that can’t be read from.
The way it works is when you or someone else tries to authenticate, the sensor makes a new mathematical representation on the fly, then queries the secure enclave to see if there is a match.
With Touch ID, there is a 1 in 50,000 chance that someone else’s fingerprint could match yours simply because the sensor only looks at some parts of the fingerprint.
And that way, it can work regardless of which part is touching the sensor. And since heredity has some influence on the fingerprint, I recommend those of you who have children to make them try unlocking your devices.
With Face ID, there’s only one in a million chance that someone else’s face could match yours, unless they are an identical twin or an almost perfect lookalike.
The way Face ID works is by projecting about 30,000 infrared dots over your face, then constructing a 3D model of it, and only storing that model. It’s because the sensor is using infrared light that Face ID works even at night.
Now, except in the case of physical security, like preventing unauthorized access to data centers, biometric authentication is used in conjunction with another form, like a PIN or a password.
Passwordless Authentication: The Future
Number 4: Passwordless authentication, so after providing your username, you authenticate either via an email loop, a physical key, or a passkey.
In all cases, the technology implemented behind the scenes has the advantage that the server doesn’t need to keep a secret.
So, first, the email loop. The server generates a unique login link or a code that can only be used once and usually expires after a short amount of time.
The other method is a physical security key. So the server creates a private key that we keep inside a physical device, and a public key that the server keeps. The beauty of the system is that it doesn’t matter if the server leaks the key, as long as we keep our private keys safe, nobody else can sign in on our behalf.
I’ve been using a YubiKey from a company called Yubico to protect a few of my online accounts. And I recently purchased another one from Token2, which works over USB C, USB A, and NFC. In addition to more connectivity, I bought a second one because it is required to have two of them when activating this level of protection on an Apple account.
The third passwordless method is called PassKeys. It’s a new technology that uses the same public and private keys method but implements that at the software level.
In other words, Passkeys can be stored in iCloud Keychain or in a password manager. I will expand on passkeys in the last segment of this episode.
Multi-Factor Authentication: Adding Layers of Security
Authentication method number five, multi-factor authentication.
So, it’s a combination of something you know, something you are, and something you have.
So, the something you know is usually a PIN, a username, and a password. The something you are is biometric authentication, so it could be your fingerprint or your face.
Now, the something you have can be another device already connected to the account that you’re trying to log into, or a device that can receive codes either directly from a server or by SMS. But it could also be a dongle or an application that generates 6-digit codes.
And finally, it could also be a physical security key or a passkey.
Creating Strong Passwords: Techniques and Tools
Okay, now let’s talk passwords. I know, I know, it’s about as exciting as watching paint dry. But bear with me. The first question is, what constitutes a strong password?
A strong password is long, and nowadays we are talking about at least 16 characters long. But it’s not enough. It needs to be complex, meaning combining digits, uppercase and lowercase letters, as well as symbols.
Lastly, it needs to be unique. The best way to guarantee uniqueness is to generate a totally random password, which is perfect for highly critical accounts for which we don’t need to memorize the password.
There are a few accounts, though, for which a strong yet memorable password makes sense. For me, it’s Google Workspace, iCloud, and my password manager.
So the next question is, how can we come up with a memorable password that is also hard to guess or brute force?
Let’s start with the first technique called the padding technique.
What we do is we start with a sentence that’s easy to remember, then we add symbols at the beginning, in the middle, and at the end. For example, I could use the sentence, “I love bananas.”
And for my Apple account password, I could choose the plus sign and then finish with the number one, since the letter A is the first letter of the alphabet.
So this would give me the password: uppercase I, the plus sign, then the word love, then the plus sign again, then the word bananas, then the plus sign again, then the number one.
If you count, it is actually 16 characters long, and it combines digits, uppercase and lowercase letters, and symbols. The chance that another human came up with the same password is extremely low.
Then you would repeat the same operation, but with a slight variation for another account. For instance, for the Google password, I could do the same thing, but instead of a plus sign, I could use the ampersand. And instead of finishing with the number one, I would finish with the number seven, because G is the seventh letter of the alphabet.
Now, even though these passwords are unique, they are not totally random, so technically they are not as strong as totally random ones.
However, since they are long enough, and most of the time the attacker doesn’t know how long and how complex it is, after trying out the most commonly used passwords and some variations of personal information that they would have gathered about me, their only last option is to actually try out all the possible combinations, starting from short passwords.
And according to the brute force password search space calculator available on the GRC website from Steve Gibson, assuming 100 trillion guesses per second (yes, that’s a lot of guesses), it would still take 1.4 hundred million centuries to crack my ILOVEBANANA password.
Of course, now that I’ve publicly explained this strategy, it is best not to reproduce it.
And just to let you know, I have a totally different strategy for my passwords. As long as I keep that strategy a secret, I feel confident that no one, even assisted by AI, would be able to guess my passwords.
Your job is to come up with a memorable password strategy that you can apply to multiple different online accounts so that the generated passwords are both strong and easy for you to reconstruct.
Another technique is called the passphrase technique.
Here we start with a sentence, but it should be much longer, like the beginning of a chapter of your favorite book. Then you would convert that sentence into a random-looking password by shortening the sentence.
Ideally, the sentence would already contain numbers.
Here, for example, I will take a simple sentence. It could be, “There are 12 months and 365 days in a year.”
So the strategy would be, for instance, to keep the first letter of every word, to keep the numbers as they are, and also to choose a way to incorporate at least one symbol.
So, for instance, in this example, I would keep the uppercase T from “There,” and then the lowercase a from “are,” the number 12, the lowercase m from “months,” and so on. Then I would convert the word “and” into a symbol. In this case, the ampersand would make a lot of sense.
So this would give me the password: uppercase T, lowercase A, the number 12, M, ampersand, and then 365, followed by lowercase D, lowercase i, lowercase a, and lowercase y. If you count, it’s actually 13 characters long, and that would constitute the baseline to which you would add before or after anything that is related to the online service of your choice.
For the Apple ID, you could add, for instance, a dash symbol and then APL, all uppercase. This would give you a very strong 17 characters long password that is almost totally random and that doesn’t contain any dictionary word.
Now, except for a few accounts, I recommend actually creating totally random passwords, especially for online accounts that have a higher risk of getting hacked.
See, I don’t worry about Google and Apple because they’ve put very strong security barriers in place. For Microsoft, I’m sorry, but I’m not 100 percent confident. And for almost everyone else, I assume that sooner or later, they will get hacked and my username and password will get leaked.
So the next question is, how can we easily create random and complex passwords?
The simplest way is to use the suggestion provided by Safari when you create your account. The reason is that the suggested password qualifies as a strong one, and on top of that, it will get saved in iCloud Keychain, which means your password will be synchronized across all your Apple devices. Now for other browsers, I don’t recommend using the browser as a way to suggest a password.
Even if the passwords that are suggested are pretty strong, it’s more the fact that the management of the password is not as secure as with iCloud Keychain.
Using Password Managers: Recommendations
And so, the second-best way to generate random passwords is to use a dedicated password manager.
The best ones work across multiple devices and have dedicated browser extensions, which is much safer when you use Chrome, Firefox, or any third-party browser.
And a third way, if you need to generate and store a password but exclusively on your Mac, so you don’t need or don’t want to synchronize it at all, then I recommend using Keychain Access.
It’s a built-in tool of macOS. You can launch it with Spotlight by typing command space and then start typing K E Y C, or you could also visit the Applications folder where you will see a Utilities subfolder from which you will be able to launch Keychain Access.
On the left sidebar, you would select the Login keychain, and then in the top toolbar on the right, you would click on an icon that looks like a square with a pen in it.
This will initiate the creation of a new item.
At the top, there is a field for the name, and if it’s an online service, this is where you will put the login URL. Otherwise, you can type the name of the service. And then, underneath, there is a field called Account Name, where you will write the username.
And to generate a password, you would click on an icon that looks like a key.
Another window will open, which is the Password Assistant. And there, from the first drop-down menu, you will choose Random. And then, under that, you will use a slider to choose the password length that you want.
Once you are happy, you close the password assistant, then you click on the add button to save it inside Keychain Access.
Anytime you need to use that password, you open Keychain Access, then you click on the Login keychain in the sidebar. You visit the search field and you type the name of the service or the account name. Then you simply right-click on the item and you choose Copy Password to Clipboard.
Another window will appear, asking you to enter your Mac user account, and then you will click on the Allow button. After that, you will be able to paste it wherever you want.
So yes, it is protected by your user account password, which means that even if a stranger were to roam inside your Mac, they could not get access to your passwords unless, of course, they know your user account password.
Whatever is stored inside the login keychain is only available from that Mac. So make sure that it is backed up by Time Machine; otherwise, you could lose them.
I’m recording this episode in July 2024, so iOS 18, iPadOS 18, and macOS 15 Sequoia are not officially out yet, but by Fall 2024, there will be another method to generate random passwords. And that will be actually through a standalone Passwords application coming from Apple.
I have played a little bit with the Mac version inside a virtual machine, and the look and feel are very similar to the Reminders app.
The iPad version will be almost identical to the Mac app.
For the iPhone version, I’m still waiting for the second or third public beta version before installing it on my old iPhone XR so that I could be able to test it more.
And so, given that Apple is about to offer a dedicated passwords management application, you might be wondering whether using a third-party password manager makes any sense, especially if you are a solopreneur fully invested in the Apple ecosystem.
And to me, the answer is yes, for a few reasons.
If your Mac is stuck at a version below macOS 15 Sequoia, then with iCloud Keychain and Keychain Access, there is a limitation that we don’t have with third-party password managers.
And the limitation is that we can only associate one URL to each item.
Now, if you have an Amazon account, you know that the same username and password are used for all the regions, so amazon.com, amazon.ca, amazon.co.uk, and so on.
And so with a third-party password manager, it’s possible to have a single item referring to all the URLs of Amazon, rather than having seven different items, which is the case for iCloud Keychain.
Another reason why it’s worth considering using a third-party password manager is the ability to create custom fields.
With iCloud Keychain, for instance, we can have the website URL, maybe a verification code, and a note, but that’s it. With third-party password managers, we can create and populate our own custom fields, like a secondary address, the recovery phone number used for receiving authentication codes, or it could be an API key generated by ConvertKit, for instance, or the OpenAI API key.
When you use iCloud Mail, if you want to configure another email client, sometimes you need to create what is called an app password. And so with a third-party password manager, you could then just create a new custom field, app password, and you add it to the same item, rather than having two or three or four different items.
And talking about items, with third-party password managers, we can also store other types of items, for instance, passport information, driver’s license information, bank account numbers, notes, documents.
With 1Password, for instance, it’s possible to attach multiple documents to a given item. For instance, in addition to my ID card information, I have attached a scanned version of both sides of my ID card in PDF format, as well as two images, one for each side. No need to visit multiple places like Apple Notes or Apple Photos. Everything is in one location.
And then, most third-party password managers are cross-platform, which could prove handy if you hire a virtual assistant who doesn’t have a Mac or an iPhone.
And finally, some third-party password managers give us the choice of the location for the server that will hold our vault. This is especially useful for folks like me whose business is registered in the EU and subject to GDPR.
So, with 1Password and Bitwarden, for instance, it’s possible, at the time that the account is created, to tell them to exclusively use servers located within the EU.
And because 1Password is headquartered in Canada, they also offer the ability to use servers located in that country, while with Bitwarden, it’s even possible to host the vault on our own server, like a Synology NAS, for instance.
And so, yes. I’ve already spilled the beans.
Based on my research, there are only two third-party password managers that I decided to use and that I can safely recommend: 1Password and Bitwarden.
1Password is the most capable and user-friendly, but there is no free version, just a free trial. The individual plan starts at $36 per year, and the family plan costs $60 per year, about $12 per person for a family of 5. I have been a long-time 1Password customer, and I absolutely love this service.
I actually have 3 subscriptions. A 1Password Teams account for EasyTECH, and two family plans. One for my family here in Luxembourg, so my children, my wife, and I, and another one for my family in Belgium, so my mom, my sister, and my cousins.
The reason that I stick with 1Password is twofold. I can unlock it using my Apple Watch, and it also supports keyboard shortcuts, making it the most efficient password manager on Mac, period.
Bitwarden, on the other hand, is perfect for people who want a free solution that offers more than iCloud Keychain, like secure notes, credit card information, and identities.
And for even more advanced features, like storing the one-time passwords, the vault health and data breach reports, as well as having 1GB of storage for encrypted file attachments, the premium individual plan starts at $10 per year, while the families plan costs about $40 per year for 6 members.
If you’re not using anything yet, my advice is to start with iCloud Keychain for at least six months. And then you could decide whether it’s good enough for you or not.
Chances are that it will be, so just keep using it. Otherwise, have a look at both Bitwarden and 1Password and choose the one that looks the most appealing to you.
If you are an Apple Watch owner, or if you are a keyboard shortcut junkie, then 1Password is hands down the best option here. It is so good to not need to enter the master password all the time, and also to quickly copy-paste the password and even the verification codes without needing the mouse at all.
All right, are you ready for the future?
Exploring Passkeys: The Next Step in Authentication
So let’s talk about Passkeys.
Imagine never having to type another password when logging into your course platform or your email marketing tool. That’s the promise of Passkeys. It’s like having a personal bouncer for each of your online accounts.
Since macOS 13 Ventura and iOS 16, iPadOS 16, our Apple devices natively support Passkeys. And since iOS 17 and macOS 14 Sonoma, it is even possible to share groups containing passwords and Passkeys with other Apple users.
And in case you’ve never heard about it, it’s a new way to authenticate ourselves by having our device pass a challenge which leverages biometric authentication, so Face ID or Touch ID.
Unlike with usernames and passwords, the website or the online service doesn’t need to store any secrets. So even in the case of a data breach, there is nothing that an attacker can use.
And on top of that, a Passkey, say for Facebook, cannot work on a Facebook lookalike phishing website because the Passkey is tied to Facebook’s domain, and so our devices cannot accidentally log us in.
And all of this makes Passkeys a promising technology.
However, two years in and they are barely in use. One issue is platform lock-in. If you store your Passkeys in iCloud Keychain, you’ll only be able to authenticate from an Apple device, not on Android, for instance.
The solution to that is to use a third-party password manager, like 1Password or Bitwarden, which can store Passkeys and work cross-platform.
Another issue is that few websites support Passkeys, and those that do still maintain the ability to log in with a username and a password.
And in the case of Google Workspace, for instance, by default, Passkeys replace the second factor of authentication, not the username and password.
And so, a Google Workspace admin has to turn on the settings for a full replacement of usernames and passwords.
And even if Passkeys are a step in the right direction when it comes to securing our online accounts, it is important to realize that it also shifts the burden to us and to the security of our devices.
Indeed, anyone able to access our devices and to reconfigure biometric authentication will be able to use our Passkeys to access our online accounts.
Final Tips and Action Plan
Okay, before concluding this episode, there’s one more thing I’d like to mention.
Given that the trend goes towards passwordless authentication methods, protecting our email accounts is more important than ever.
In other words, the password to access your inbox needs to be super strong and complex. And also, multi-factor authentication must be enabled while avoiding SMS at all costs, ideally using a physical security key.
Bonus tip number one, make a list of all your business-critical online services. For instance, your domain registrar, your website host, your invoicing and accounting platform, the email marketing service that you use. Then in another column, write down which email address serves as the username. This will give you clarity and visibility of what needs to be protected the most.
Bonus tip number two. If you are a Google Workspace user, leverage the ‘Sign in with Google’ feature as much as possible, that way bad actors will be obliged to attack your Google account first, which hopefully is better protected than the website that you will be logging into.
And bonus number three, if you use ‘Sign in with Google’ and 1Password, you are in luck because 1Password can remember which online service has been configured with ‘Sign in with Google’, and even tell you which Google account is associated. Another reason why I am so bullish about 1Password.
So to recap, here is your action plan for fortress-level authentication.
First, enable two-factor authentication on all your crucial accounts.
Number two, leverage iCloud Keychain or invest in a reputable password manager. I recommend 1Password or Bitwarden.
Number 3, start using passkeys where available. You will be ahead of the curve.
And number 4, most importantly, secure your email accounts like Fort Knox. They are the keys to your digital kingdom.
Remember, implementing strong authentication isn’t just about protecting your business. It’s about protecting your peace of mind. You’ve worked hard to build a solopreneur business. Don’t let weak security be your Achilles heel.
And as explained in previous episodes, it’s only half the battle against cyber threats. The other half is keeping your devices secure and, most importantly, your Mac.
Download the Mac Security Checklist
How? By going through the checklist that I covered in episode 99.
So, if you haven’t downloaded the checklist yet, remember to visit macpreneur.com/msc for Mac security checklist.
If you need help going through it, just listen to or watch episode 99.
Your future self and your clients will thank you later for taking proactive steps against cyber threats.
If you enjoyed this episode, please share it with a fellow solopreneur and DM. My handle is @MacpreneurFM.
Conclusion and Upcoming Episodes
So that’s it for today. In the next episode, I will discuss how solopreneurs can secure their business website.
So make sure to subscribe or follow this podcast to get it automatically next week.
Before saying goodbye, I wanted to give you a heads up about what will happen at the end of Season 5, which will be concluded with Episode 107, released on July 25th.
Since I take a few weeks of vacation beginning in August, there will be a break in the regular programming.
It doesn’t mean that the podcast feed will be empty, as I will rebroadcast the most popular and evergreen episodes from Season 1, which many of you haven’t listened to yet or have most probably forgotten about.
So for Season 6, which will start in September, I have decided to switch back to an interview format with one episode already recorded and a few more in the preparation stage.
In fact, if you’d like to be a guest, just visit macpreneur.com/apply, fill out the application form, and I’ll get back to you within a few days.
I would love to chat with you about how you run your solopreneur business on your Mac and what tips, tools, and strategies you have put in place to be more efficient.
Once again, visit macpreneur.com/apply.
I can’t wait to feature you in an upcoming episode of the Macpreneur podcast.
And until next time, I’m Damien Schreurs, wishing you a great day.
Thank you for listening to the Macpreneur Podcast. If you’ve enjoyed the show, please leave a review and share it with a friend right now.






